If you play any role in the great ecosphere that is the IoT of today, then you have seen the articles.
Industrial cellular routers are at risk, heralds The Hacker News.
Vulnerabilities could expose thousands of industrial organizations to remote attacks, shouts SecurityWeek. And most recently, SC Media railed that
certain router vulnerabilities pose a hacking risk to critical infrastructure. IoT cybersecurity concerns are enough to keep network managers up at night, and even potentially put a damper on the meteoric growth of the Internet of Things.
Don’t blame the media. They are just doing their jobs. And that awareness is helping to break through a risky and long-standing mindset that cybersecurity IoT breaches are isolated or uncommon. Today, no organization deploying connected devices can rest easy in the notion that, “it won’t happen to us.” We must acknowledge that it can happen to absolutely any organization, anywhere in the world — even financial institutions, which presumably have the very latest in cybersecurity protocols and compliance frameworks in place.
In IoT and cybersecurity, there are critical steps every single operation can and should put into place to not only establish a foundation of good security hygiene, but also ensure that all connected devices under corporate jurisdiction can be updated as new critical vulnerabilities come to light.
Key Concepts in IoT Cybersecurity

Let’s start with the important principles of IoT cybersecurity. You may be wondering: What is cybersecurity in IoT, and what are some examples?
As most people today are aware, the IoT, or Internet of Things, is a term to describe the vast universe of connected devices. This includes smart home devices and smart buildings, as well as industrial devices, smart transportation and smart city technologies and more. IoT cybersecurity involves strategies and practices to ensure that all connected and wireless devices — including routers, gateways, embedded communication modules, and all devices that integrate these connected technologies — are designed or programmed to deter cyberattacks.
For example, if a cellular router deployed in a corporate office or on a moving bus or train does not require authentication to receive outside data, then a "bad actor" can take advantage of this lack of security to send data that alters the functionality of that device.
Here are some key concepts in IoT cybersecurity that can help organizations define a security plan to protect their corporate data:
- All connected devices can be hacked. This is because a cybercriminal — or even an inside operator who makes a mistake — can exploit the fact that devices are talking to one another. Weak passwords, software vulnerabilities, lack of updates, social engineering tactics like phishing or social media scams, insecure network connections, risky default configurations, malware, and lack of user awareness relating to any of these issues can lead to connected devices being compromised.
- There is no single responsible party in cybersecurity; it takes a village. Everyone along the chain from manufacturers to end users plays a role in device security.
- Manufacturers must build in security from the ground up and provide methods for maintaining security over the life of the product.
- Network administrators must establish and reinforce security practices through authentication, role-appropriate access and password practices for all users.
- End users must comply with all cybersecurity requirements and use of secure passwords.
- Companies must create a security guild or “devsecops” (Developer Security Operations) team that drives ambassadors across the business to spread user awareness training around information security.
- It’s important to develop a corporate security mentality to have security practices closer to the edge of development and operations, as it’s no longer a singular functional team.
- Cyberthreats are ever evolving, so security measures must be agile. Hackers are creative and skilled, and new threats are constantly emerging, which means you must have a method in place of proactively monitoring and managing devices. Device manufacturers (OEMs) and network managers must build and deploy devices with the capability to be remotely updated as new threats are identified.
Industry Resources to Support IoT Cybersecurity

The good news is that there is a vast community of cybersecurity experts, and a wealth of tools and capabilities available to help organizations put best practices in place, monitor for breaches, and respond quickly.
It’s important to understand the vulnerability and adversarial landscape frameworks like CVE’s, CWE’S, MITRE ATT&CK Framework and OWASP TOP 10.
CVE’s (Common Vulnerabilities and Exposures), CWE’s (Common Weakness Enumerations), MITRE ATTA&CK (Adversarial Tactics Techniques and Common Knowledge) Framework, and OWASP (Open Web Application Security Project) Top 10 are all cousins in cybersecurity, but they serve different purposes.
- CVEs are a publicly available dynamic dictionary of information security vulnerabilities and exposures of hardware or software run by a nonprofit organization, The MITRE Corporation. These are known risks that every organization can and should address. CVEs highlight known vulnerabilities in software and systems, exposing potential weaknesses that can be exploited by malicious actors. Taking them seriously ensures proactive measures can be taken to mitigate these vulnerabilities, reducing the risk of cyberattacks and data breaches. Additionally, CVEs facilitate the sharing of information and collaboration among security professionals, enabling the development of effective patches and updates. Ignoring CVEs can lead to severe consequences, including financial losses, reputational damage, and compromised privacy and security for individuals and organization.
- CWE is a community-driven list of common software weaknesses. It provides a very thorough classification of software security weaknesses that empower development to identify and mitigate risks during the software development lifecycle.
- MITRE ATT&CK Framework is an internationally available knowledge base matrix that provides insights into the tactics, techniques, and procedures (TTPs) used by attackers or advanced persistent threat groups (APT’s) during cyber intrusions. It provides guidance for understanding and categorizing adversarial behavior to enable organizations to test and prepare for known attack paths.
- OWASP Top 10 is an evolving list of the most critical web application security risks like code injection, cross site scripting (xss), and broken authentication to name a few. OWASP Top 10 delivers valuable information to leverage development to improve their security posture of web applications like a Remote Management system for IoTs.
These frameworks collectively help organizations comprehend, prioritize, and mitigate risk and are integrated into many security technology stacks today.
Critical IoT Device Security Best Practices

In the evolving landscape of IoT cybersecurity, it may seem like there is no hope of putting adequate security protections in place. After all, the hackers keep outsmarting the smartest corporations in the world, right?
We have more good news. There are important cybersecurity steps, and these practices transcend the evolving nature of cyber threats.
- Require permission and credentials for access to all devices. This was called out as an issue in one of the media articles. This best practice should be in place as a matter of course for all devices. Credentials must be required for access to any device on a network; and importantly, these must not be provided as defaults. As mentioned, the responsibility of cybersecurity belongs to everyone.
- Adopt a multi-layer security approach that avoids any single point-of-failure. Passwords and authentication are important. But to address other avenues of access, corporations should deploy devices with built-in security measures like secure boot, protected ports, and configuration monitoring. There’s far more to discuss here. Contact us if you would like to work with a Digi representative to address your organization’s needs.
- Deploy devices with the ability to proactively update them over their lifecycle. This critical step requires the ability to perform secure over-the-air updates as new CVEs are identified. Whether you are deploying devices with embedded connectivity modules (such as medical devices, IoT wearables, EV charging stations, or farming equipment) — or you are deploying cellular routers and gateways (such as in transit systems, traffic management, manufacturing automation or enterprise networking), you need remote monitoring and management capabilities to monitor for threats, automatically remediate threats such as configuration changes, and deploy regular firmware updates. Again, Digi representatives can help you to identify the right approach
- Establish physical device security. Devices that can access the corporate infrastructure should be kept in locked cabinets. Physical IoT device security is crucial for protecting against unauthorized access and tampering. Robust physical security measures such as tamper-evident seals, secure enclosures, and strong authentication mechanisms help prevent physical attacks and tampering attempts. Physical security also involves protecting devices during transportation, storage, and installation. By ensuring the physical integrity of IoT devices, organizations can minimize the risk of data breaches, maintain the privacy of sensitive information, and safeguard the overall functionality and reliability of their IoT ecosystem.
- Provide ongoing education across the organization. Human beings are fallible creatures, and this means everyone on the planet that uses connected devices needs to be reminded periodically of the role they play in securing devices.
- Teach your teams how to identify social engineering threats.
- Send reminders about what phishing attempts look like.
- Remind employees not to allow non-badged visitors to follow them into secure office buildings.
- Work with a total solution vendor that integrates security best practices as well as monitoring and management services. In other words, don’t just buy devices and deploy them. Work with a solution vendor that provides the ability to proactively manage devices. This may encompass a few best practices for secure development and production testing to ensure confidentiality, integrity, and availability is in check.
- Static Analysis, which is a method used in software development to examine code without executing it that aids in finding flaws with variables and vulnerabilities associated with the codebase.
- Dynamic Analysis, which is a method used in software development to examine code during runtime when executed and may be conducted during test or production to discover unexpected behavior that leads to security vulnerabilities and unexpected behavior.
- Open source dependency analysis, which is a method used in software development that checks open source libraries and components used in the software to identify security vulnerabilities like CVE’s and CWE’s or licensing issues.
- Infrastructure scans that support your software development which may be for IaaS, Containers, Servers to ensure your build environments don’t have any entry points for malware or malicious code to get into the software of firmware builds.
- Penetration testing is a methodology to assess the security posture of a system, network, or application conducted internally by cybersecurity staff or externally through a pentesting firm.
- Bug Bounty which is a third party vendor that supports continuous testing on a system, network, or application that rewards researchers on the Bugbounty for valid discoveries.
- Remote Management systems that can aid in FOTA — (firmware over the air) to ensure field devices have a way of patching a fleet to stay on top of the vulnerability lifecycle.
How Digi Supports Your IoT Cybersecurity Goals
Naturally, we’ll share our story here, and what differentiates Digi as an IoT solution vendor. Digi has been developing connected systems for nearly four decades, and we have built numerous processes and teams around cybersecurity integration, monitoring and management.
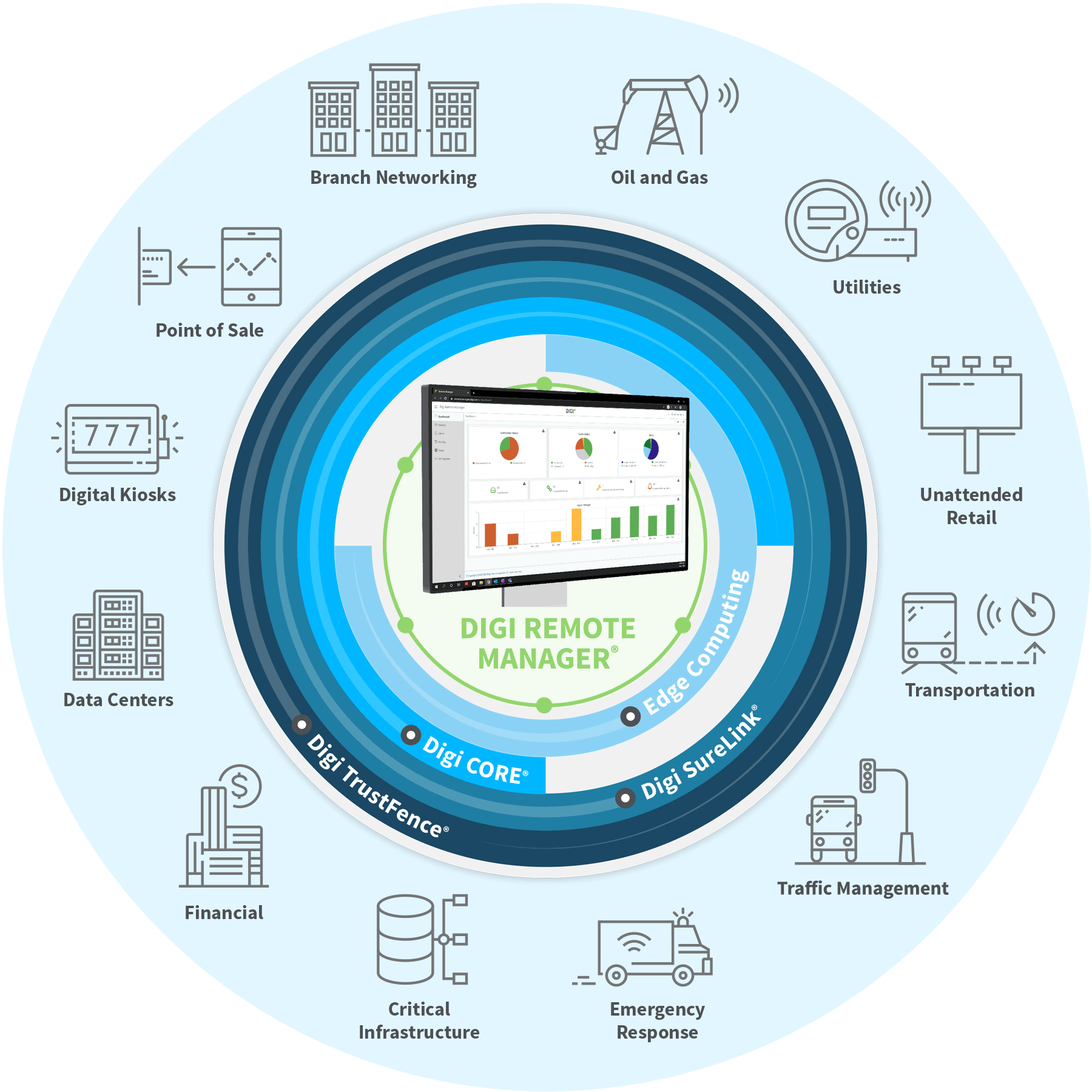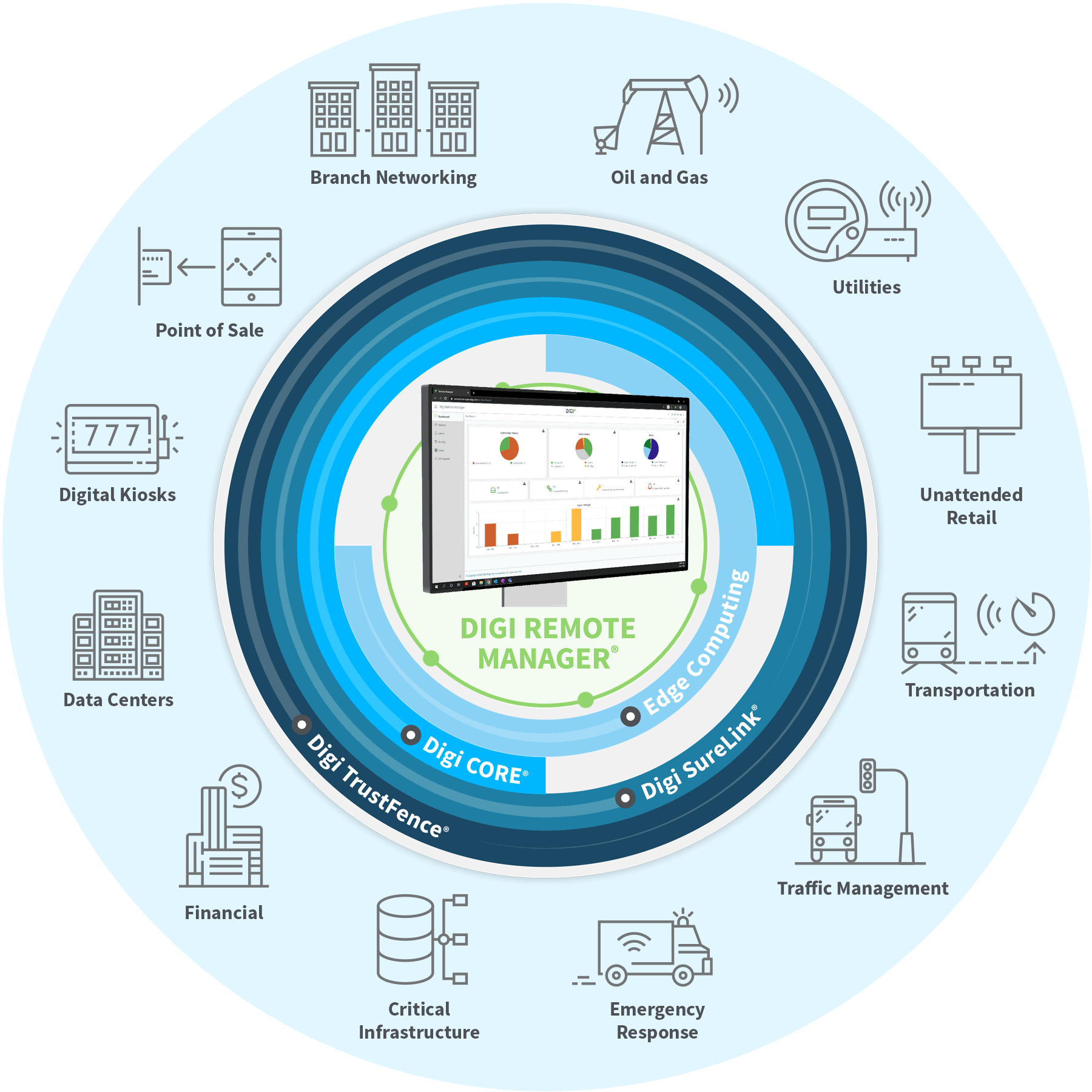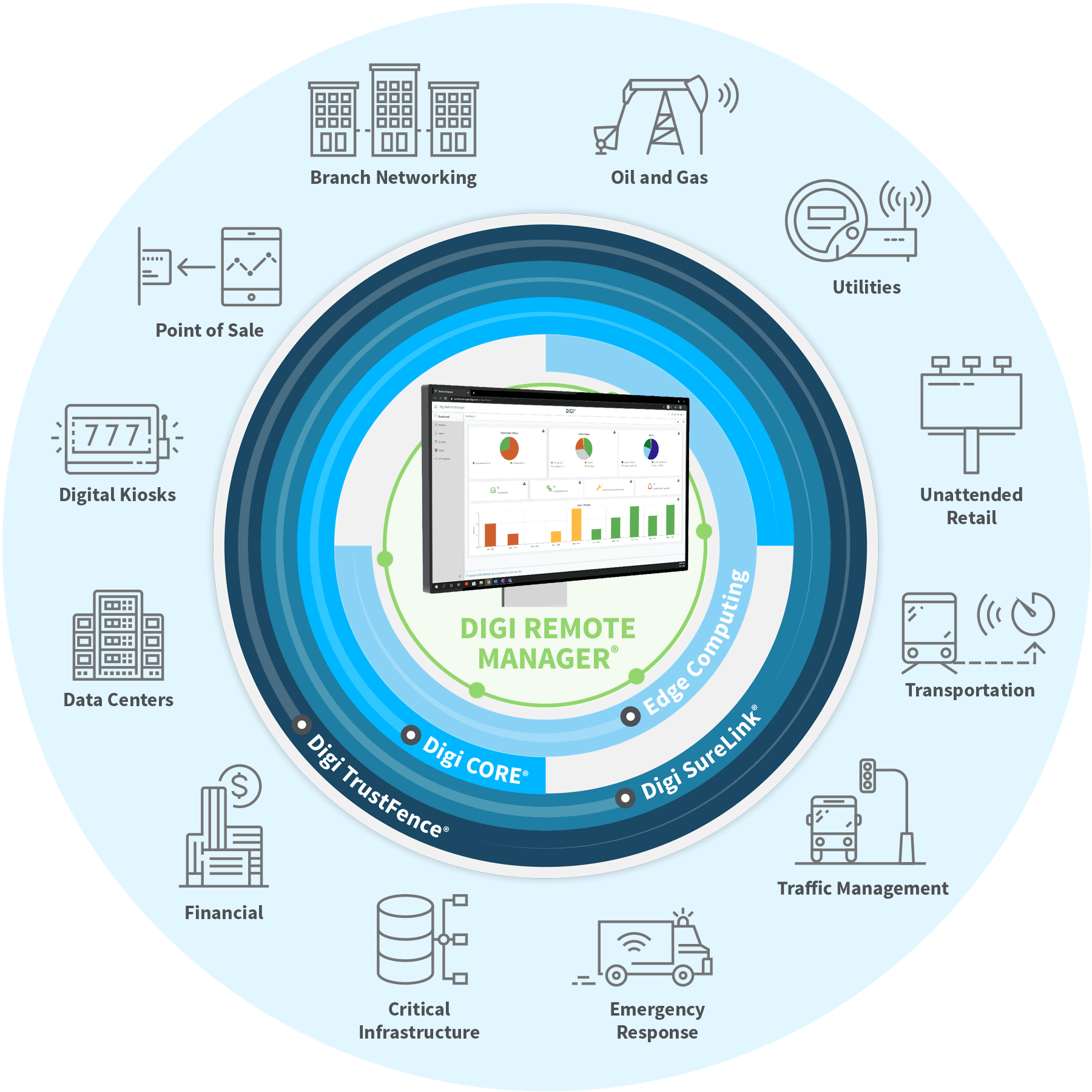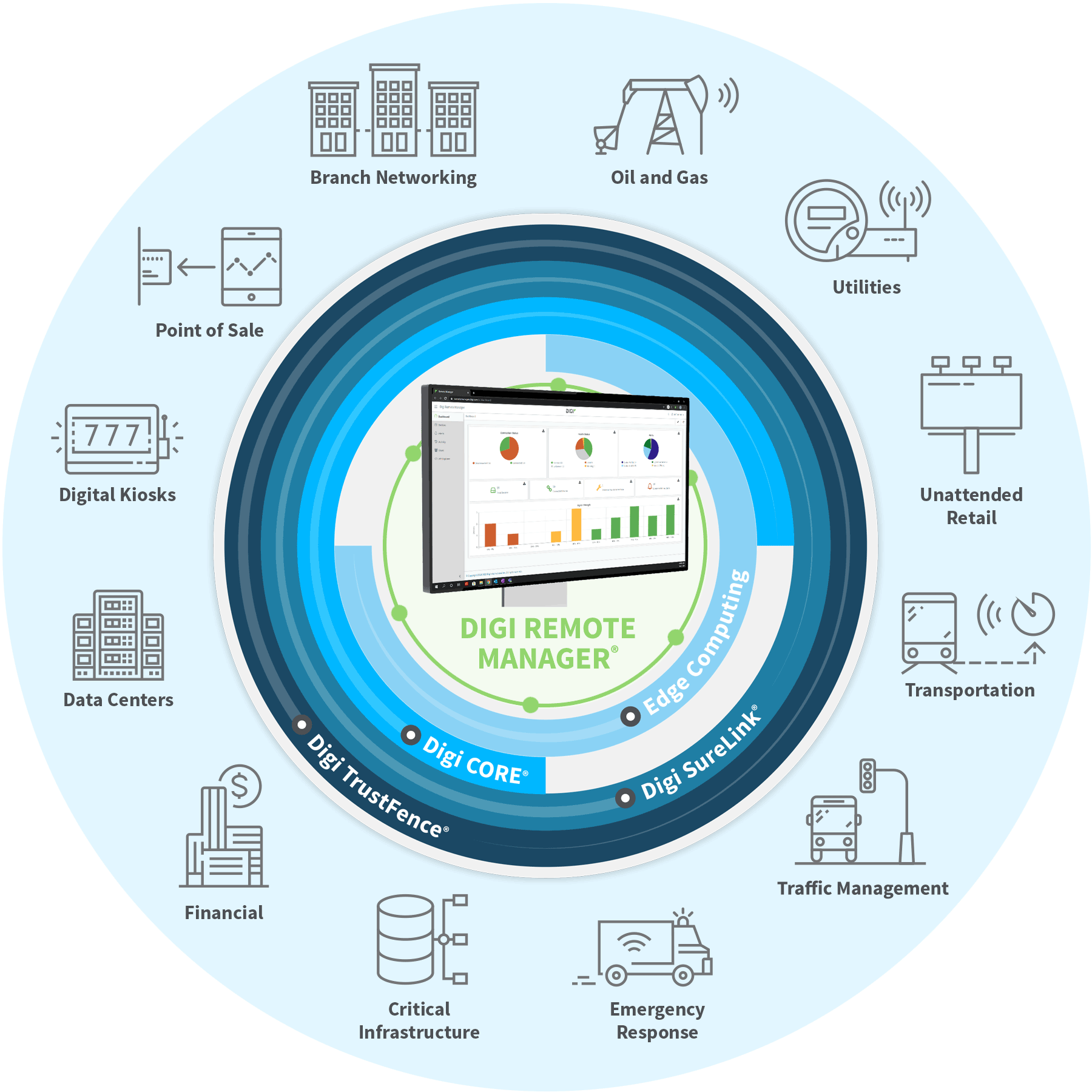
At the forefront of our security integration is Digi TrustFence®, a security framework that provides multiple points of security in our devices. Our cellular routers, for example, integrate this framework to ensure that these devices have built-in security out-of-the-box, as well as features to support further security integration at the time of deployment and end-use.
Digi Remote Manager®, our remote monitoring and management platform, offers monitoring, automated management to detect and remediate unauthorized configuration changes, and the ability to remotely manage and update dozens, hundreds or thousands of devices with a few button clicks.
For Digi ConnectCore®, our ecosystem of embedded system-on-modules, tools and services, we offer Digi ConnectCore Security Services for security management over the lifecycle of deployed products, as well as Digi ConnectCore Cloud Services for ongoing device monitoring and maintenance. And our Digi XBee® devices have long integrated the ability to perform over-the-air firmware updates.
Additionally, Digi has a devsecops team responsible for monitoring security industry trends and emerging vulnerabilities for proactive management of our devices and transparent communications with our customers.
While “one and done” is not a phrase that describes an adequate approach to cybersecurity today, there is much that organizations across the IoT ecosphere can do to establish rigorous security policies and procedures, and ensure they have the ability to proactively maintain devices for life. Digi can help!
Next Steps